Connect to AWS Organizations
Connect Hyperglance to your Organization at the root or Organizational Unit level and monitor all your accounts at once.
This is a step-by-step guide showing how to connect Hyperglance to monitor accounts in your AWS Organization.
To follow these steps you should be an admin or have sufficient permissions to access your AWS Organization management account and be able to deploy StackSets across your entire Organization.
Step 1) Grant Hyperglance read-only access to your AWS Organization.
There are three options for this depending on your deployment scenario:
Scenario A: Hyperglance is deployed into the management account itself
In this scenario granting access can be done by modifying the IAM Role attached to the Hyperglance instance:
In the AWS Console -> Find the instance -> Under the Security tab click the Role:
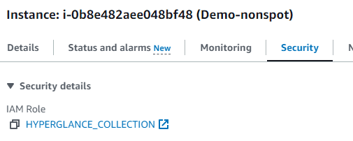
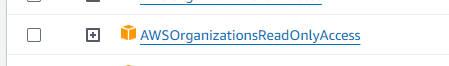
Attach a policy to this role and select the AWS managed policy called AWSOrganizationsReadOnlyAccess:
Scenario B: Hyperglance is deployed into an AWS Account that is not the AWS Organizations management account
In this scenario you will need to create a cross-account trusting IAM Role. Create the Role in your AWS Organizations management account and set it to trust the account that Hyperglance resides in.
Attach a policy to this role and select the AWS managed policy called AWSOrganizationsReadOnlyAccess:

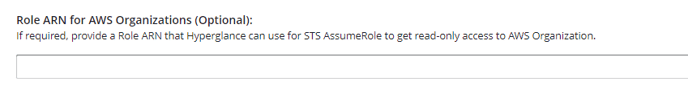
Later we will paste the the ARN of that role into Hyperglance:
Scenario C: Hyperglance is deployed outside of AWS or in a different AWS partition.
For this scenario you will first need to create an IAM User in the management account and set up access and secret keys for that user. Save the keys as will later paste them into Hyperglance.
The user should be assigned a role that grants STS:AssumeRole.
Next, follow the procedure for Scenario B.
Step 2) Deploy the IAM Role across your Org that Hyperglance will use to connect into each account.
a) Log into your AWS Organizations management account.
b) Go to CloudFormation
c) Go to StackSets
d) Deploy our cross-account role: https://github.com/hyperglance/deploy/tree/master/AWS/CloudFormation/XAccount
For convenience we also host it in an S3 bucket here: https://hyperglance-deploy-repo-public.s3.amazonaws.com/AWS/CloudFormation/XAccount/Hyperglance-xaccount-role.json
A couple of things to note:
1. StackSets deploy into every account in the organisation except for the root management account. If you wish to include this account in Hyperglance then simply re-deploy the Cloudformation template again a regular Cloudformation Stack in the root account.
2. Hyperglance will be unable to connect in to any accounts that do not have this role deployed.
Step 3) Add the Organization to Hyperglance
a) Open the Hyperglance UI
b) Go to Settings
c) Click "Connect to Amazon":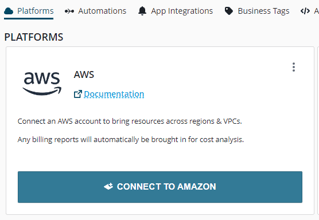
d) Name the connection alias anything that you want
e) Select "AWS Organizations":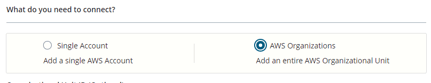
f) Provide an Organizational Unit ID if you want Hyperglance to connect to a specific point in the org tree. Otherwise leave this blank (or enter the root ID) to point Hyperglance to the root of the org tree.
g) If you followed Scenario B or Scenario C under Step1 above then you will have a Role ARN to paste in here (otherwise leave blank):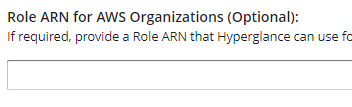
h) If/When AWS has finished deploying the StackSets from Step2 above then check this box: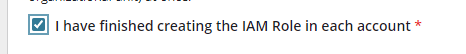
g) If you followed Scenario C under Step1 then expand Access Keys and enter those next: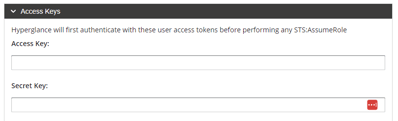
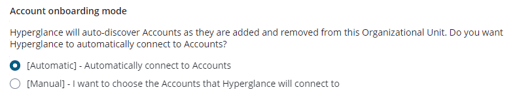
h) Decide how Hyperglance should treat any new accounts added to the Org at a later date. Should it "Automatically" start ingesting their resources? Or should it leave those accounts for you "Manualy" activate?
i) Select the AWS Regions, this will apply to all the accounts in the Organization: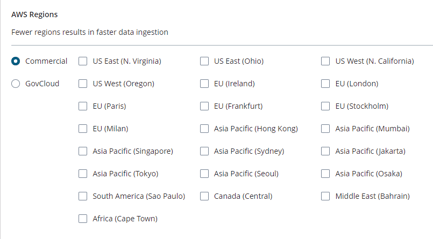
j) "Organization Groups" is an optional way to group connections together. This can be left blank.
k) Click Submit
Step 4) Wait for ingestion to complete
All being well you should now see your org tree represented on the Settings page:
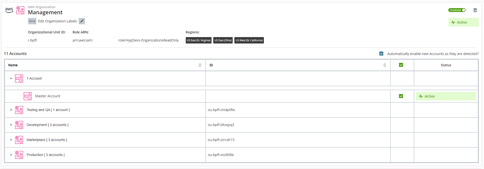
The Status column should show the status and health of the connection. Including whether the ingestion is in-progress and/or whether there are any IAM issues.
