How to set up Hyperglance via the AWS Marketplace
Find out the optimal way to set up Hyperglance, when deploying via the AWS Marketplace
In this article, you'll learn:
Deployment Options
Hyperglance needs access to the AWS API in order to collect data. By default, the AWS endpoints are public IPs. There are various methods of securing access to Hyperglance, you will be led by your security posture as to which one to use.
The order in terms of each option's complexity is as follows:
1. The Hyperglance instance has a Public IP, inbound access is limited using a security group.
2. The Hyperglance instance has a Public IP, inbound and outbound access is limited using a security group and a Network Access List (NACL).
3. The Hyperglance instance is placed behind a NAT Gateway or Load balancer.
4. The Hyperglance instance runs in a private subnet and has multiple Virtual Private Cloud Endpoints configured for access to the AWS API via private IPs.
You can find more information about these 4 AWS deployment options here
You can also find out more about how Hyperglance works with AWS here
Step-by-Step Guide
1. Go to Hyperglance's AWS Marketplace listing
2. Choose the appropriate number of resources and then 'Continue to Subscribe'
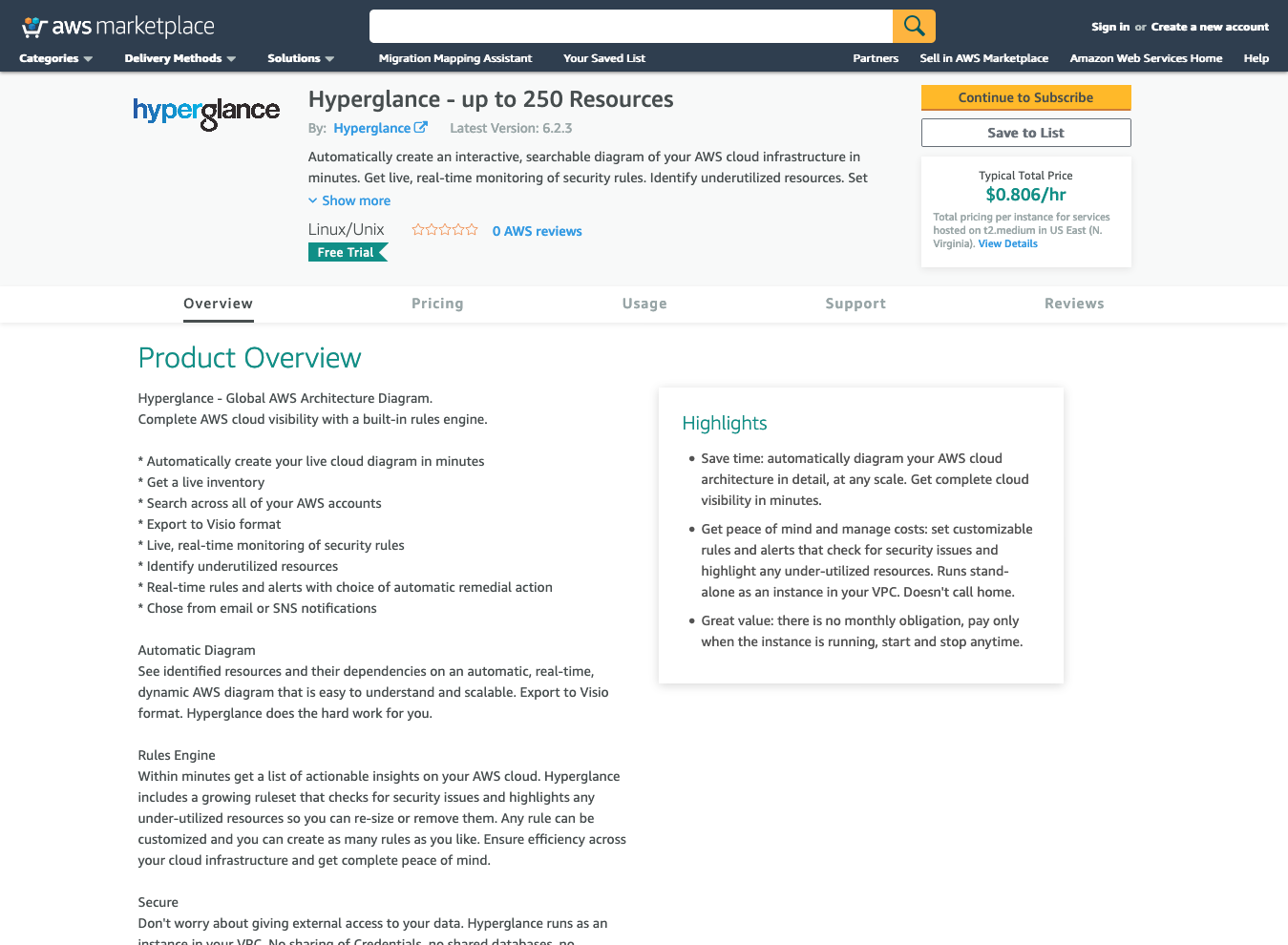
3. Accept the terms
.png?width=688&name=Screenshot%20(6).png)
4. This will take us to a page describing the next steps, read and return to the launch page
.png?width=688&name=Screenshot%20(7).png)
5. Select 'Continue to Configuration'
.png?width=688&name=Screenshot%20(8).png)
6. It will take a few minutes before the subscription is ready. Once the subscription is live, choose the region you want the Hyperglance instance to be created in.
.png?width=688&name=Screenshot%20(9).png)
7. Select 'Continue to Launch'
.png?width=688&name=Screenshot%20(10).png)
8. Select ‘Launch CloudFormation’
.png?width=688&name=Screenshot%20(11).png)
9. Once you have selected 'Launch CloudFormation', select to 'Launch'
.png?width=688&name=Screenshot%20(12).png)
10. You'll be taken to CloudFormation in your AWS console. There is nothing to change here as the S3 template is already selected. Select 'Next'.
.png?width=688&name=Screenshot%20(13).png)
11. In the 'Specify stack details' page you have the option to name the CloudFormation stack, and decide on things like assigning a public IP.
Hyperglance needs access to the AWS API in order to pull down the information needed.
Be careful when choosing the VPC & Subnet you want Hyperglance to be deployed in. It's possible to mismatch the VPC & Subnet causing the stack creation to fail.
.png?width=688&name=Screenshot%20(14).png)
12. Once that’s set, select 'Next'
.png?width=688&name=Screenshot%20(15).png)
13. You’ll then get the option to tag tags. In the example below, we have added 'Hyperglance' as a 'Name' tag.
.png?width=688&name=Screenshot%20(16).png)
14. Scroll down to the bottom of the page, select 'Stack creation options' and select 'Disabled' for 'Rollback on Failure'. This will allow you to see which steps fail if the stack has issues.
After you've done that, select 'Next'..png?width=688&name=Screenshot%20(17).png)
15. On the review screen, scroll down to the bottom to accept the disclaimer and select 'Create stack. This enables CloudFormation to start creating the Hyperglance instance.
.png?width=688&name=Screenshot%20(18).png)
16. You’ll be taken to the CloudFormation stack console page. It'll take up to 10 minutes to finish the instance creation.
.png?width=688&name=Screenshot%20(19).png)
17. Once the stack has been created successfully, go to the 'Outputs' tab. This'll show you how you can connect to the Hyperglance Instance.
.png?width=688&name=Screenshot%20(20).png)
18. By default, Hyperglance’s password is the instance name, so copy that and then click on the link to go to Hyperglance.
Be careful when copying and pasting the instance name. Sometimes there is an extra space at the start/end of the string that will prevent you from authenticating successfully.
19. Proceed to the Hyperglance console page (acknowledging the browser warning)
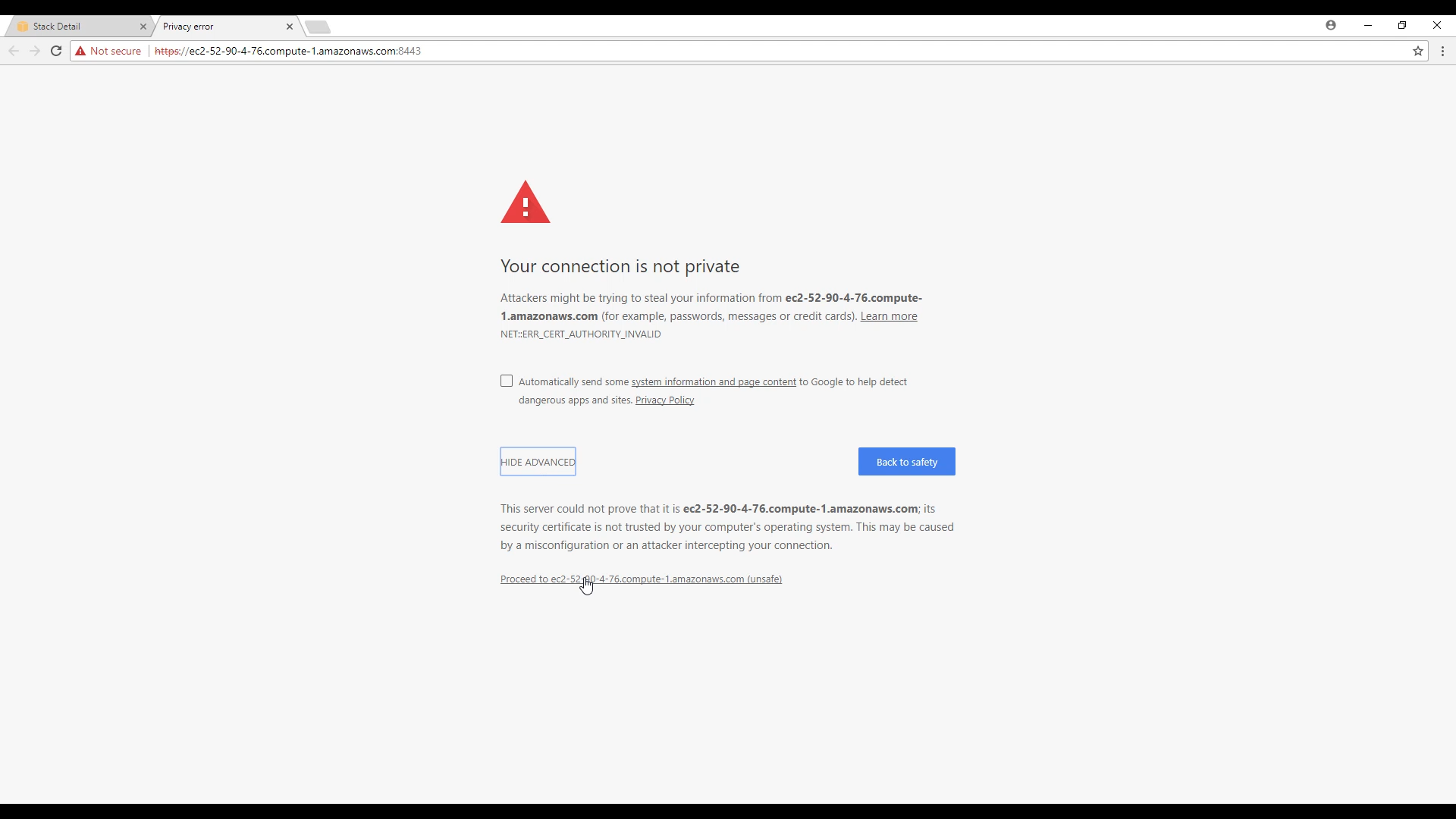
20. You can now see, and log in to, the Hyperglance console. The default userid is ‘admin’ and the password is the Hyperglance instance-id.
Make sure you use HTTPS (port 443) to connect to Hyperglance

21. After logging in go to Settings > Platforms click CONNECT ACCOUNT for AWS:

22) In the dialog provide a memorable alias for the connection.
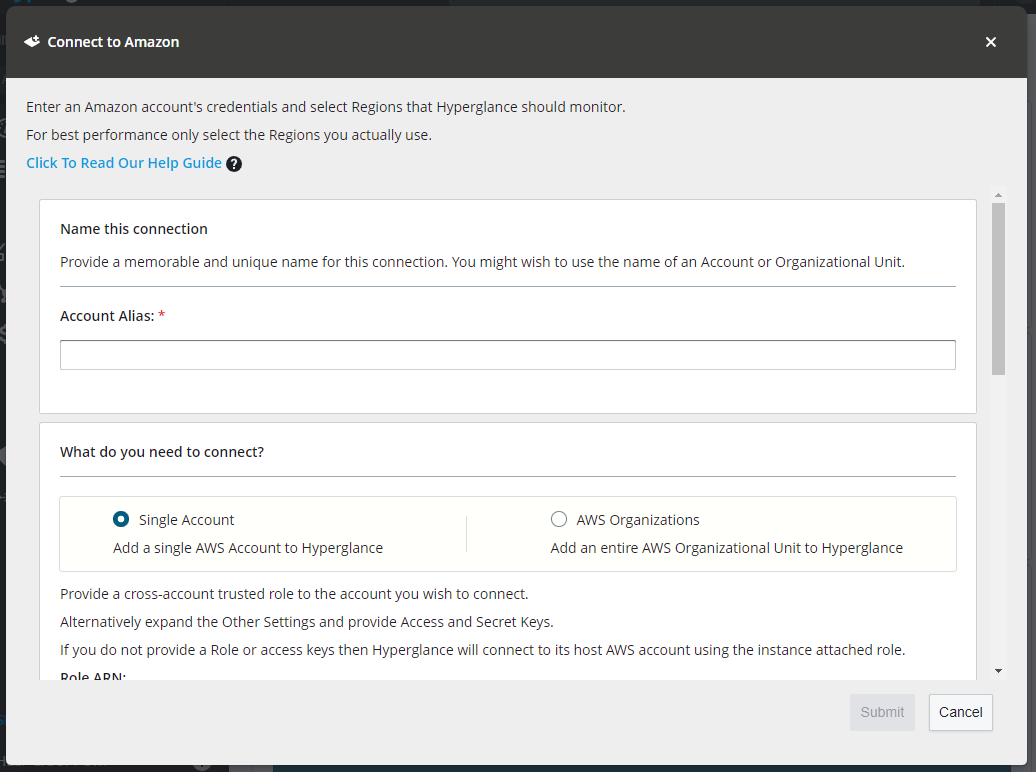
You can add as many accounts as you need with a great deal of flexibility in how you connect to those accounts. However the easiest way to get up and running quickly from the marketplace is use the defaults in the form:
- Provide an alias
- Select "Single Account"
- Leave the Role ARN and other settings blank or at the their defaults
- Choose at least 1 region to connect to.
- Press Submit
23. Hyperglance will automatically update to the latest version, assuming you are connected to the internet. If you weren't connected during your setup, make sure you use these instructions to update Hyperglance to the latest version. All user data is retained through an update, including authentication credentials, rules, and tag-view keys.
Deploy Hyperglance Rule Automations for AWS
Pre-Requisites
Before you can deploy automations you will need:
- Terraform CLI - Install instructions
- AWS CLI - Install instructions
- IAM permissions configured on the Hyperglance Instance - See below.
IAM Permissions
The IAM Policy on the Role associated with the Hyperglance EC2 Instance will need the following permissions added:
"s3:PutObject",
"s3:GetObject",
"s3:ListBucket",
Quick Start
-
Follow the pre-requisite steps above.
-
Connect the AWS CLI to the AWS account that hosts Hyperglance by running: aws configure
Note: You will need an AWS IAM access and secret key.
Example:
$ aws configure
AWS Access Key ID [None]: ENTER_YOUR_ACCESS_KEY_HERE
AWS Secret Access Key [None]: ENTER_YOUR_SECRET_KEY_HERE
Default region name [None]: us-east-1
Default output format [None]: json -
Clone our repo or download the zip
$ git clone https://github.com/hyperglance/aws-rule-automations.git
-
Configure the stack:
Edit: aws-rule-automations/deployment/terraform/automations/main.tf
Set the hyperglance_identity_arn equal to the ARN of the IAM Role that is attached to your Hyperglance EC2 instance.
It might be something like arn:aws:iam::012345678901:role/HGRole
(This is a security feature that helps limits access to the S3 bucket to the Hyperglance instance)
-
Deploy the stack:
Terraform will prompt for the region you wish to deploy to and for final confirmation.
$ cd aws-rule-automations/deployment/terraform/automations
$ terraform init
$ terraform apply -
Once complete, the bucket name and lambda function ARN will be returned:
Apply complete! Resources: 8 added, 0 changed, 0 destroyed.
Outputs:
bucket_name = "hyperglance-automations-lucky-marmoset"
lambda_arn = "arn:aws:lambda:us-east-1:0123456789:function:hyperglance-automations-lucky-marmoset"The lambda ARN is required to configure automations across accounts
Copy these into the Hyperglance UI: Settings ➔ Automations ➔ Automations for AWS ➔ S3 Bucket Name
-
That's it - Automations are now enabled!
- Within Hyperglance click on any rule or visit the Advanced Search page to start exploring automations features.
- If you need automations to run on resources from other AWS Accounts then continue on to follow our multi-account guide below.
Adding Hyperglance automation permissions to your accounts
To grant the automations Lambda access to resources in other AWS accounts you will need to create a special cross-account role in each of those accounts:
-
Edit aws-rule-automations/deployment/terraform/xaccount_role/main.tf
- Set the lambda_arn to the arn of the lambda function which was given as an output in the main account configuration.
-
Connect to an AWS Account where you wish to deploy the Role:
- Run: aws configure
- You will need AWS IAM access and secret keys for this account.
-
Deploy the Role:
$ cd aws-rule-automations/deployment/terraform/xaccount_role
$ terraform init
$ terraform apply
Customizing Automations
Easily add your own automations or modify existing ones!
Automations are written in Python3, each one is a self-contained Python (.py) file. Find them here: https://github.com/hyperglance/aws-rule-automations/tree/master/lambda/automations
To add a new automation:
- Add a new .py file
- Implement the hyperglance_automation() function with logic for your automation.
- Implement the info() function to inform the Hyperglance UI about your automation:
- Name,
- Description,
- Any UI inputs it needs from the user,
- A list of compatible resource types.
- Re-deploy the terraform stack with terraform apply
- Done: Your new automation will be immediately available and ready to use in the Hyperglance UI.
Having Problems?
If you run into any issues setting up Hyperlglance, please log a support ticket and one of the team will be in touch to give you a hand.
