How to set up SSO with SAML for Azure Entra ID
Find out how to set up SSO, with Azure Entra ID (Formerly Azure Active Directory), using SAML
Hyperglance 💙 Azure
As an Azure user, there's a high chance you could be utilizing Hyperglance to manage your cloud, and you'd be in good company. Our success stories come from all over the globe, including NASA, Vodafone, Cisco, and the U.S. Air Force.
Hyperglance users quickly come to rely on our powerful and ever-growing suite of cloud management tools, including:
- Real-time, interactive diagrams of your AWS, Azure & Kubernetes infrastructure
- Automatic inventory documentation with export options
- Powerful search capability, across your entire inventory and its metadata
- Cost management, security & compliance monitoring, and automation/remediation
- Azure Government support
For more information, visit hyperglance.com
How To Set Up SSO With SAML for Azure Entra ID
1. Log in to the Azure Portal and search for Active Directory

2. Start with configuring groups, these will be associated with Hyperglance Roles at a later stage. Select Groups:

3. Click New Group and let's call this group Hyperglance Admins.
Refer to our Role-Based Access-Control (RBAC) Documentation to learn about other kinds of user besides admins.

4. Add members to your group by clicking No members selected and then selecting some users:


5. Click Create:

Repeat the previous steps to create additional groups for other Hyperglance Roles if needed. For the list of Roles supported by Hyperglance please refer to the document describing Role-Based Access-Control (RBAC) used in Hyperglance
6. In Entra ID select Enterprise applications:

7. Click New Application:

8. Select Non-gallery application:

9. Give the application a name and click Add:

10. From the left side Select Single sign-on and pick the SAML option presented:


11. On the VM, generate Service Provider (SP) metadata by running this script (/usr/bin/mellon_create_metadata.sh), be sure to adjust the IP address as appropriate for your setup:
mellon_create_metadata.sh https://188.166.207.211 https://188.166.207.211/saml
The 1st parameter: The SAML Entity ID - This can be any URI that uniquely identifies your Hyperglance install, using the IP address is a good way to do that.
The 2nd parameter: The URL to the SAML endpoint for your Hyperglance VM. Must be set to: https://{yourHyperglanceVM}/saml
The IP address or DNS name you use here must be the one that your browser would use to reach the Hyperglance VM because SAML works using browser redirects!
If the script was successful you will see an output like this:
Output files:
Private key: /etc/httpd/mellon/sp.key
Certificate: /etc/httpd/mellon/sp.cert
Metadata: /etc/httpd/mellon/sp.xml
Empty IdP metadata file: /etc/httpd/mellon/idp.xml
Host: 188.166.207.211
Endpoints:
SingleLogoutService: https://188.166.207.211/saml/logout
AssertionConsumerService: https://188.166.207.211/saml/postResponse
The script has generated an sp.xml file and an empty idp.xml we will need to use these in the next steps.
12. Upload the sp.xml file from the VM to the Azure portal using the "Upload metadata file" option:


13. After the upload it should have populated the Entity ID and the Reply URL. No other changes are needed so just click Save and close the form:


14. Replace the empty idp.xml file on the VM with the Federation Metadata XML you can download from the Sign sign-on page in the Azure portal:

Make sure you name the file idp.xml and place it at /etc/httpd/mellon/idp.xml
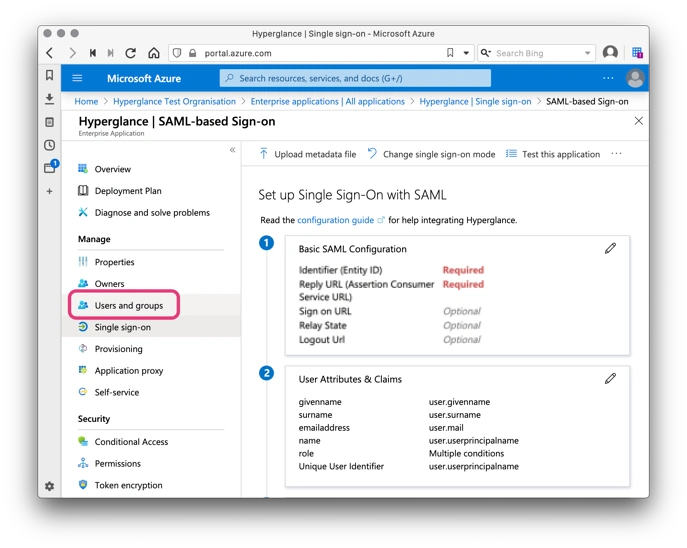
15. Click to edit User Attributes & Claims:

16. Click Add new claim:

17. Name the new claim role (Hyperglance expects that name!) and expand the Claim conditions section:

18. For User type select Any and for Scoped Groups choose the Hyperglance Admin group we created earlier:

19. Set the Source to Attribute and type in HyperglanceUser;HyperglanceAdmin as the Value.
Note: There must not be any spaces around the semicolon that separates the Hyperglance role names.

If you added any additional groups at the steps 3-5, then add them with additional claim conditions as above and assign them the appropriate set of Hyperglance roles.
20. Click Save

21. Navigate to Users and groups and click Add user

22. Select users and/or groups that you will allow to access the Hyperglance application. Hyperglance will also show in their apps access panel (e.g http://myapps.microsoft.com ).

When ready click Assign:

23. We now configure the Hyperglance VM to enable SAML. Edit the file /var/lib/data/hyperglance/config.env and set the SAML_ENABLED flag to true.
24. Restart the services running on the VM for our changes to take effect:
sudo docker-compose -f /etc/docker-compose.yml up -d
25. Azure will now suggest you test your new SSO configuration. Try it, it should now work!
During your first visit to Hyperglance, you may be prompted by your browser to acknowledge that Hyperglance (by default) ships with a self-signed SSL/TLS certificate.
If this happens accept the warning by clicking Advanced and then Proceed (Note different browsers may show this differently):


If you are also asked to resubmit the form data then choose to accept.
All being well you should now be logged in to Hyperglance!
